The internet has drastically transformed the way we conduct our daily lives, providing immense convenience in everything from banking to shopping. However, with this convenience comes the growing threat of cybercrime, which evolves alongside advancements in digital technology. Terms like “russianmarket.to,” “dumps,” “RDP access,” and “CVV2 shops” are becoming common in cybersecurity discussions, often linked to illicit activities in the darker corners of the internet.
This article will delve into these terms, explaining what they mean, why they’re becoming a significant cybersecurity concern, and what steps can be taken to protect personal and corporate data in an increasingly digital world.
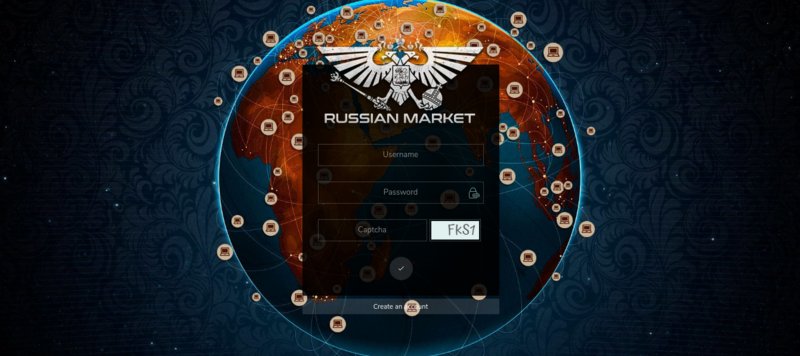
What Is russianmarket.to?
The term “russianmarket.to” refers to an online marketplace often associated with the sale of stolen or illegal digital assets. These assets can include credit card details, banking information, dumps (i.e., data extracted from the magnetic stripe of a credit card), and access to compromised computers or networks through Remote Desktop Protocol (RDP). Sites like russianmarket.to are part of a broader cybercrime ecosystem that facilitates the trading of stolen information and hacking tools among criminals.
Although not as well-known as some other platforms in the dark web, russianmarket.to is becoming increasingly popular because it offers a wide range of illegal services and goods, catering to a growing community of cybercriminals. The platform is known for being user-friendly, allowing even individuals with minimal technical knowledge to purchase illicit data or services.
Understanding Dumps and How They Are Used
“Dumps” refer to the raw data extracted from a card’s magnetic stripe, including the card number, expiration date, and sometimes even the cardholder’s name. This information is used in “card-present” fraud, where fraudsters clone the magnetic stripe of a stolen card and use it in physical transactions. The demand for dumps has surged in underground markets like russianmarket.to, as they provide cybercriminals with a method to commit fraud without necessarily hacking into a company’s online infrastructure.
There are several ways criminals obtain dumps. Skimming devices are a common method, where small gadgets are placed over card readers at ATMs or point-of-sale terminals to capture card data. Another method involves hacking point-of-sale (POS) systems to intercept card details during transactions.
RDP Access: A Gateway to Corporate Networks
RDP (Remote Desktop Protocol) access allows users to control a computer over a network connection, and it is widely used for remote work or troubleshooting. Unfortunately, it has also become a valuable asset in the cybercriminal underworld. RDP access is sold on marketplaces like russianmarket.to, often providing buyers with the ability to control compromised systems within corporate or government networks.
Cybercriminals can use RDP access to deploy malware, ransomware, or further exploit a network’s vulnerabilities. In many cases, they leverage this access to steal sensitive information, such as employee credentials or intellectual property, or to launch Distributed Denial of Service (DDoS) attacks. Additionally, RDP access allows attackers to create persistent backdoors in the system, making future breaches easier.
The sale of RDP credentials on black-market platforms is a growing issue for organizations that have not implemented strong cybersecurity measures. Poorly secured RDP access, such as using weak or default passwords, can leave companies vulnerable to cyber-attacks. The increased popularity of remote work following the COVID-19 pandemic has only exacerbated this problem, as more companies rely on RDP without always ensuring that it is properly secured.
The Role of CVV2 Shops
CVV2 refers to the three-digit code found on the back of most credit cards. CVV2 shops specialize in selling stolen credit card information that includes not only the card number and expiration date but also the CVV2 code, which is often required to complete online transactions. While having just the card number can be used for some fraud, possessing the CVV2 code significantly increases the likelihood of successfully completing unauthorized transactions.
Cybercriminals harvest CVV2 data through several methods. One of the most common tactics is phishing, where fake emails or websites trick users into providing their card details. Keylogging malware and data breaches of legitimate e-commerce platforms are other methods used to obtain CVV2 codes.
The combination of card numbers, expiration dates, and CVV2 codes provides cybercriminals with the full suite of information they need to make fraudulent online purchases or sell the data on illicit markets. Websites like russianmarket.to are integral to the distribution of this stolen data, contributing to the increasing rates of online credit card fraud globally.
The Impact of These Cybercrime Activities
The activities facilitated by sites like russianmarket.to have far-reaching consequences, affecting both individuals and organizations. Financial losses due to credit card fraud can be significant, and individuals may suffer long-term harm if their personal information is used to open fraudulent accounts or make unauthorized purchases. For businesses, a security breach that exposes customer data can result in reputational damage, loss of customer trust, and regulatory fines.
Moreover, the sale of RDP access can be especially damaging for companies, as it can lead to a full-blown ransomware attack. These attacks can cripple organizations, making it impossible to access critical files and systems until a ransom is paid. Even when companies can restore their systems from backups, the operational downtime and reputational damage can be devastating.
How to Protect Against These Threats
The rise of platforms like russianmarket.to underscores the need for robust cybersecurity measures. Both individuals and organizations can take steps to protect themselves from becoming victims of cybercrime:
- Use Strong Passwords and Two-Factor Authentication (2FA): Weak passwords are a major vulnerability, especially for RDP access. Using strong, unique passwords for each account and enabling 2FA wherever possible can significantly reduce the risk of unauthorized access.
- Regularly Monitor Financial Transactions: Keeping an eye on bank and credit card statements can help detect unauthorized transactions early. In cases where fraud is detected, quick action can limit financial losses.
- Implement Security Best Practices for RDP: Companies using RDP should ensure that it is properly secured by using strong passwords, enabling account lockout policies after several failed login attempts, and using VPNs for added security.
- Stay Vigilant Against Phishing: Phishing remains one of the most common ways cybercriminals obtain card details. Being cautious about clicking on links in unsolicited emails or entering personal information on unfamiliar websites can prevent data from being compromised.
- Update Systems Regularly: Regular software updates are essential for patching security vulnerabilities. Both individuals and organizations should ensure that all devices and systems are updated with the latest security patches to prevent hackers from exploiting known vulnerabilities.
Conclusion
As the digital world continues to evolve, so too do the methods used by cybercriminals. Marketplaces like russianmarket.to play a significant role in the dissemination of stolen data and hacking tools, creating a lucrative underground economy that thrives on the exploitation of weak cybersecurity measures. The rise of dumps, RDP access, and CVV2 shops highlights the need for vigilance and proactive security practices in both personal and corporate settings. By taking steps to secure sensitive data and networks, individuals and businesses can reduce the risk of falling victim to cybercrime.